You may have heard of Data Breaches and the fallout from them, but have you heard of the governing bodies that aim to prevent those from happening?
NIST is the National Institute of Standards and Technology, a unit of the U.S. Commerce Department. Formerly known as the National Bureau of Standards, NIST promotes and maintains measurement standards. It also has active programs for encouraging and assisting industry and science in developing and using these standards.
The frequency and intensity of cyberattacks are continually increasing, but there is hope. There are a few Cybersecurity industry compliance requirements. Still, I’d call them more ‘protocols’ since they are always growing and evolving to adapt to new security risks.
What are the data breach risks?
According to the 2020 Data Breach Investigations Report
Errors definitely win the award for best-supporting action this year. They are now equally as common as Social breaches and more common than Malware and are genuinely ubiquitous across all industries. Only Hacking remains higher, which is due to credential theft and use, which we have already touched upon. In Figure 14, you can see that since 2017, Misconfiguration errors have been increasing.
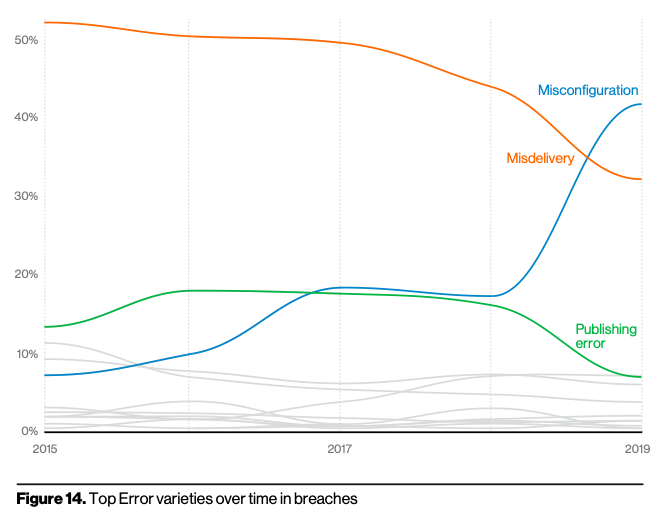
The fact that we now see errors becoming more apparent in other industries could mean we are getting better at admitting our mistakes instead of simply sweeping them under the rug. Of course, it could also mean that since so many of them are caught by security researchers and third parties, the victims have no choice but to utter “mea culpa.” A security researcher has become the most likely Discovery method for an error action breach by a significant amount being over six times more likely than it was last year.
What is compliance?
Compliance is defined as “the action or fact of complying with a wish or demand.” In IT, this must be distinguished as a practice that establishes risk-based controls to PROTECT the privacy, integrity, and accessibility of possessed information.
There are several well-known regulatory standards, including the Health Insurance Portability and Accountability Act (HIPAA) and the Payment Card Industry Data Security Standard (PCI DSS). Many of these can overlap in any IT centered business
How to create a risk assessment plan
The First step is to identify where your security vulnerabilities are – this is what will determine where compliance needs to be improved.
To create a risk assessment plan, you must:
- Identify all of your firm’s information systems, networks, and information that they access.
- Assess the risk level of each data type and determine where high-risk data is stored, transmitted, and collected.
- Analyze the risk by using the risk = (likelihood of breach x impact)/cost formula.
- Determine to transfer, refuse, accept, or mitigate the risk.
You want to continually monitor new threats to respond to them before they inflate into a problem.
IF YOU DON’T RESPOND TO A KNOWN VULNERABILITY, YOU CAN BE SUED FOR NEGLIGENCE!
Okay, So How Do I Get Cybersecurity Compliant?!
Understanding and outsourcing Cybersecurity tasks are commonly referred to as CSaaS or Cybersecurity as a Service. Looking for this service can be daunting, and you don’t have to go through the process alone. You might consider hiring a consulting company such as
Consult Our Source
It can relieve a lot of the operation strain out of transforming your company into a compliance abiding machine!


Comments are closed